Using RunZero to monitor Certificate Expiration
Managing TLS Certificate Renewal with RunZero
Purpose and TL;DR
I’m sure most people reading this are familiar with Let’s Encrypt (“LE”), the tool originally created by the EFF to democratize accessibility to both the privacy and trust that SSL and TLS certificates provide, without the $100-$150 per year price tag. Like many other #self-hosting and #homelab enthusiasts, I run a couple services that retrieve the TLS certificate via Let’s Encrypt, and many commercial services are using these certificates due to their ease of use through auto-renewal.
This article goes over implementing equivalent monitoring using the RunZero service at the free-tier, and in so doing, discovers that Chromecasts are pulling down certificates with a mere 48 hour Time To Live.
About Let’s Encrypt
Let’s Encrypt adoption has been astronomical over the decade since it’s been launched. Eye-balling the let’s encrypt stats shows something like a 25-30% year-over-year. With over 550M websites using a Let’s Encrypt-issued certificate and 6M certs/day, the service has really reached a substantial portion of the #Internet.
Certificate Expiration
Previously, if your certificates were not renewing for some reason, you would receive an email warning about the pending expiration. In early 2025, LE began sending out notices that they would discontinue this service[1], providing a recommendation to use Redsift’s free tier. Instead, I figured I would use my own RunZero instance containing the entire inventory of my computing assets. With RunZero scanning then network from both the inside and out, this is a perfect tool to use.
RunZero at Home
While RunZero is an asset discovery and inventory tool for enterprise security and IT teams, the company generously offers a nearly full-featured version of their product for running at home. I’m not sure who started this trend, but I love this trend of enabling #homelab environments with commercial-grade capabilities, which many, such as Splunk and Corelight have done. Since RunZero is scanning all my systems and enumerating their services, it should be trivial to use it to warn me about pending certificate expiration.
Monitoring Services with RunZero
It’s beyond the scope of this to describe how to configure and operate continuous monitoring with RunZero; suffice it to say that the Explorers scan on a frequent basis[2] and update the inventory accordingly. In the SaaS portion of the service, correlations, data analysis and searches can be performed. Alerts are available, but only at the enterprise tier.
Examining Host Attributes
Clicking into a host will bring forth a screen with all the attributes that RunZero knows about it. And this will usually be a LOT of data. RunZero leverages many innovative techniques to collect as much information about an asset as possible; take a look at some of their blog posts. Among this data is information about each network-addressable service running on the host and any certificates associated with them. This is where we can

Crafting the queries
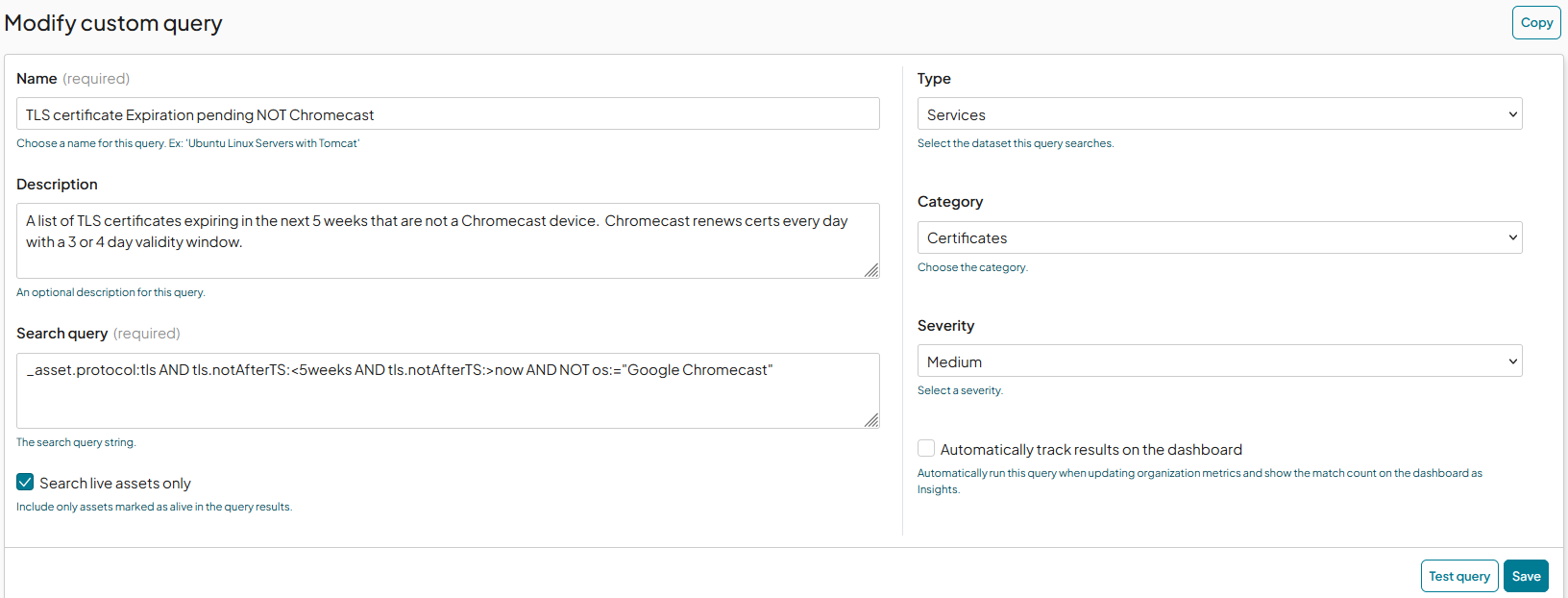
Here is the final query I used.[3]
alive:t AND (_asset.protocol:tls AND tls.notAfterTS:<5weeks AND tls.notAfterTS:>now AND NOT os:="Google Chromecast")
Let’s break this down:
alive:tI’m only concerned with assets that RunZero considers to be alive_asset.protocol:tls AND tls.notAfterTS:<5weeksthis is the key search, matching any hosts that have a certificate expiring in the next 5 weeksAND tls.notAfterTS:>nowI speficically don’t want expired certificates; I will place that in a separate query.AND NOT os:="Google Chromecast"Through this exercise, I discovered that the Chromecast renews certificates with only 2-day lifespan, which means they are always about to expire. I ignored these devices
For use in a dashboard widget, we need to make this a saved query. Under the Queries section from the navigation tree, create a new query. The fields are pretty self-explanatory
- Give it a name
- Add a description so you know what this is supposed to do a year from now
- Add our query to its box. You do not need the
alive:tbecause there is a checkbox making it redundant. - We are searching a service, so make sure the Query type is “Services”
- Change the severity, if you like.
Adding widgets to the dashboard
The default RunZero dashboard is filled with lots of information, but what’s the fun in a tool if we don’t tweak it to reflect our own environment?
Create the widget
Now we create a custom widget.
- On the dashboard, click “widgets” in the upper left, and then select “Custom” on the dialogue box
- Click Create Widget
- Specify the query created above
- Done!
Now just add your newly created widget to a dashboard you check regularly and you’ll be apprised of pending certificate expirations! For example, now that I have these have been added to the dashboard, I have a nice view of any pending or past certificate expirations.
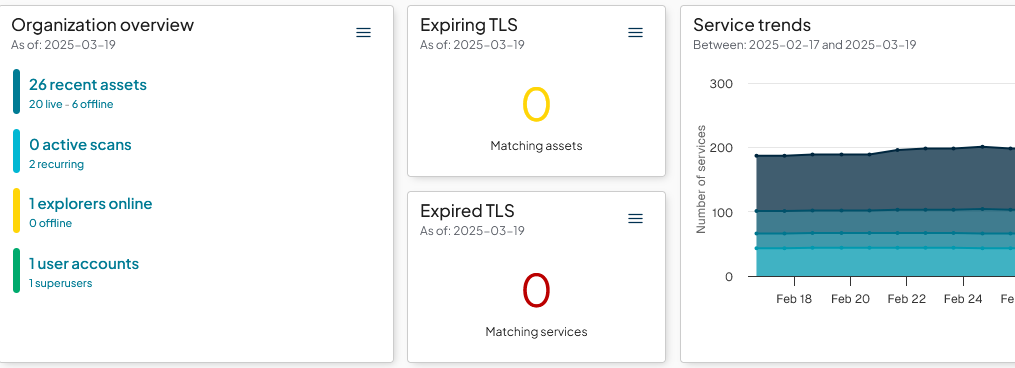
One thing to note is that the Chromecast appears to have a number of certificates across eight or so distinct services. Some of these have extremely long-lived certificates, as opposed to the very short-lived ones.
THE END! Have fun creating your own queries and dashboards on your #homelab instance of RunZero, and if you like this, I recommend their monthly podcast, the RunZero Hour, which is just a good chat between the people making the product enthusiastically talking about asset identification and vulnerabilities.
Worried about expiring SSL certificates? 😩
Learn how RunZero can help you track & manage them effortlessly! 🚀 Check out my latest blog post for a step-by-step guide on crafting custom queries and dashboards to stay ahead of those expirations. ➡️ [link to your blog post]
#cybersecurity #infosec #sysadmin #homelab
Originally mentioned in this toot when I first noticed this. ↩︎
At the outset, I was scanning weekly, however, in the course of this project, I changed it to be every 30 hours to have more up-to-date data. ↩︎
RunZero has a number of pre-defined Queries that can be accessed by the navigation tree on the left. I used this to start with their generic TLS pending expiration query and then tweaked it for my purposes. ↩︎